
Impact of the Unknown – Identifying the Blind Spots


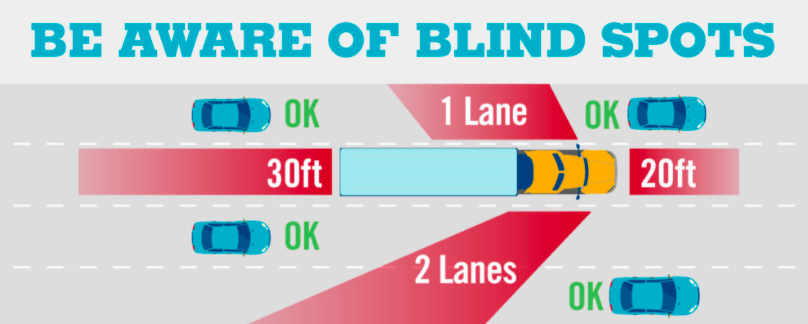
We know that there are blind spots on the road for any driver. As shown in the image above, the red colored areas are blind spots, that evade the driver’s vision and the impact of it can be of huge…
Do you know there are such blind spots in an IT Environment as well? Yes, there are many blind spots and the impact of it can be on various levels. The impact results in additional spending of money, effort, impact on performance, causes security compromise, impacts end-user experience and satisfaction and so on.
Let us understand some of those blind spots and the impact of it in an IT Environment,
In a server, for e.g., a web server, there could be a lot of applications running without the knowledge of the Application Owner or the Server Owner. These applications, either background or foreground processes consume CPU, Memory and Disk space, which are originally allocated and planned for the actual business application that is intended to run in that web server. This results in performance bottlenecks and even server crashes.
It is important to be watchful of the inflow and outflow communication between servers and devices. This may unearth new devices and new servers which are not under the purview of the server and application owner. This helps in planning the landscape, which otherwise are completely out of sight.
Whenever there is an unusual communication, appropriate measures must be taken, for e.g., if there is unusual transformation of bytes, or if there is a communication to a new port on a different server, measures must be taken to avoid potential risks.
Software licenses are brought for specific purposes, but when it is not managed or tracked properly, the licensed software could be running on those servers or desktops or laptops in which the software is no longer needed. The impact of that is that the organization may end up paying for additional licenses.
All ports in a server are properly restricted as part of hardening. Over time, due to various change requests ports are opened for new requirements. However, after the requirements are closed the ports are left unused and unnoticed. These open ports are vulnerable to hacking.
As server, laptop and desktop owners install the software from OEM and open sources, the number of applications, software in a device can increase manifold. And when these software and open sources face vulnerabilities, it is practically not possible to identify the specific version across all servers, desktops and laptops. Even before the organization takes measures on the vulnerability front, these assets are compromised by hackers.
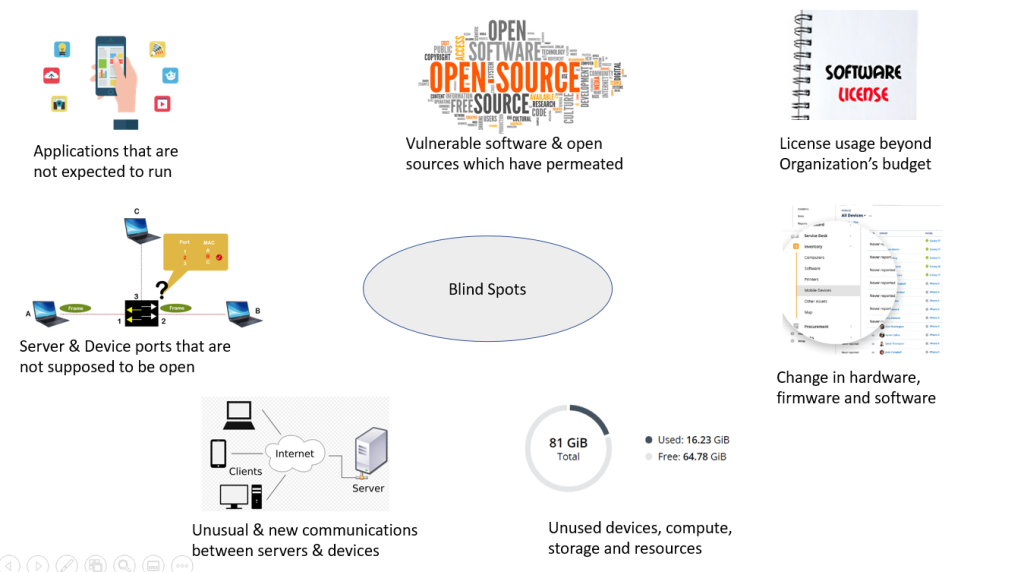
Either physical or virtual server, the compute and storage must be watched for optimal usage. Many times, few servers in an environment are over utilized whereas there are lot of servers left under-utilized. This could result in performance impact due to lack of resources. The same could happen in a VDI environment, there are users who need higher configuration of compute which can be adjusted with those users who are not using their VDI resources effectively.
When there are changes in RAM, number of CPU cores, in disk or mount volume, installation of new software, or upgrade of existing package, installation of new patch, firmware auto upgrade, etc. it is important to know the impact of these in the upstream and downstream of the environment. These changes could cause server failure, and it can impact or cause failure in the end-to-end journey of the application transaction and so on.
It is important to have full control of your IT environment, so that you can identify the blind spots and take necessary proactive actions on them. In order to uncover these blind spots, end-to-end discovery of environment is required, ZIFTM‘s Discovery module provides the agentless discover for
1) Devices and its relationship
2) Servers and its relationship
3) Applications and its relationship between servers and network devices
4) Control over Inventory and asset
5) Be aware of change in hardware, firmware and software
Watch out this space of for series of article on Discovery and how it can help organization to overcome the impact of blind spots

Suresh has 20 years of experience in Native Applications, Web, Cloud and Hybrid platforms from Engineering to Product & Program Management. He has designed and hosted monitoring solutions. At GAVS, he heads the ZIF Monitoring and ZIF Discovery Platform. He has been instrumental in amalgamating components to structure the Environment Performance Management suite of ZIF Monitor.Suresh enjoys playing badminton with his children. He is passionate about gardening, especially medicinal plants.
Please complete the form details and a customer success representative will reach out to you shortly to schedule the demo. Thanks for your interest in ZIF!